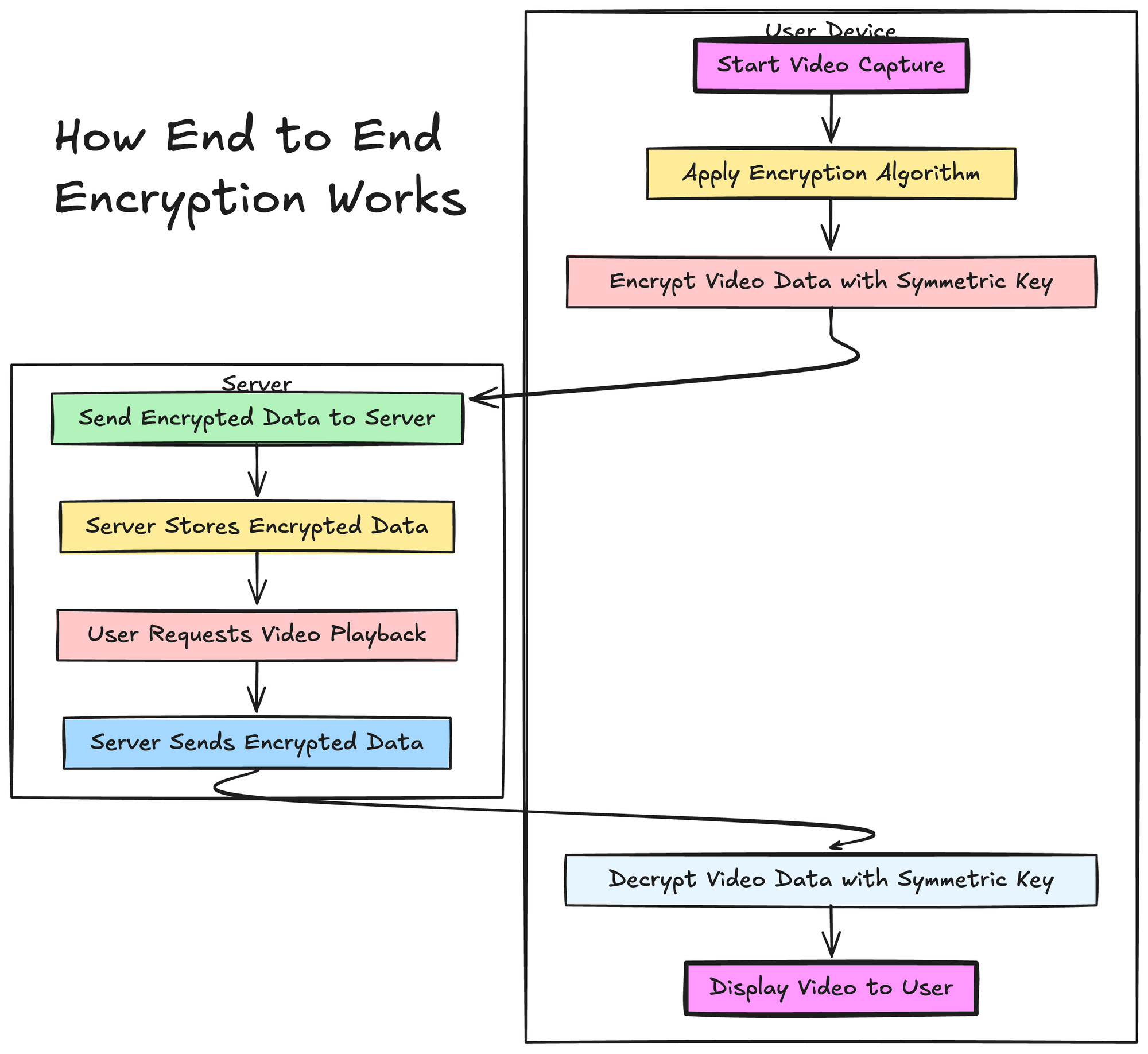
In this article we are going to learn about end to end encryption in video. The end to end encryption is a process where data that is being transferred from one user to another across a communication channel remains confidential and tamper proof from outside, this also includes the providers of the communication service
That is the providers of the communication service cannot have access to data which the users are communicating with each other
In end-to-end encryption the data is encrypted from the senders side and remains encrypted as it passes through servers and devices of the communication service provider and reaches the recipient where it is dycrypted.
This ensures that the service provider or any other intemediary or if there is any leakage or a hacker has hacked has the intransit data these cannot access the data because it is encrypted and can only be decrypted by the recipient.
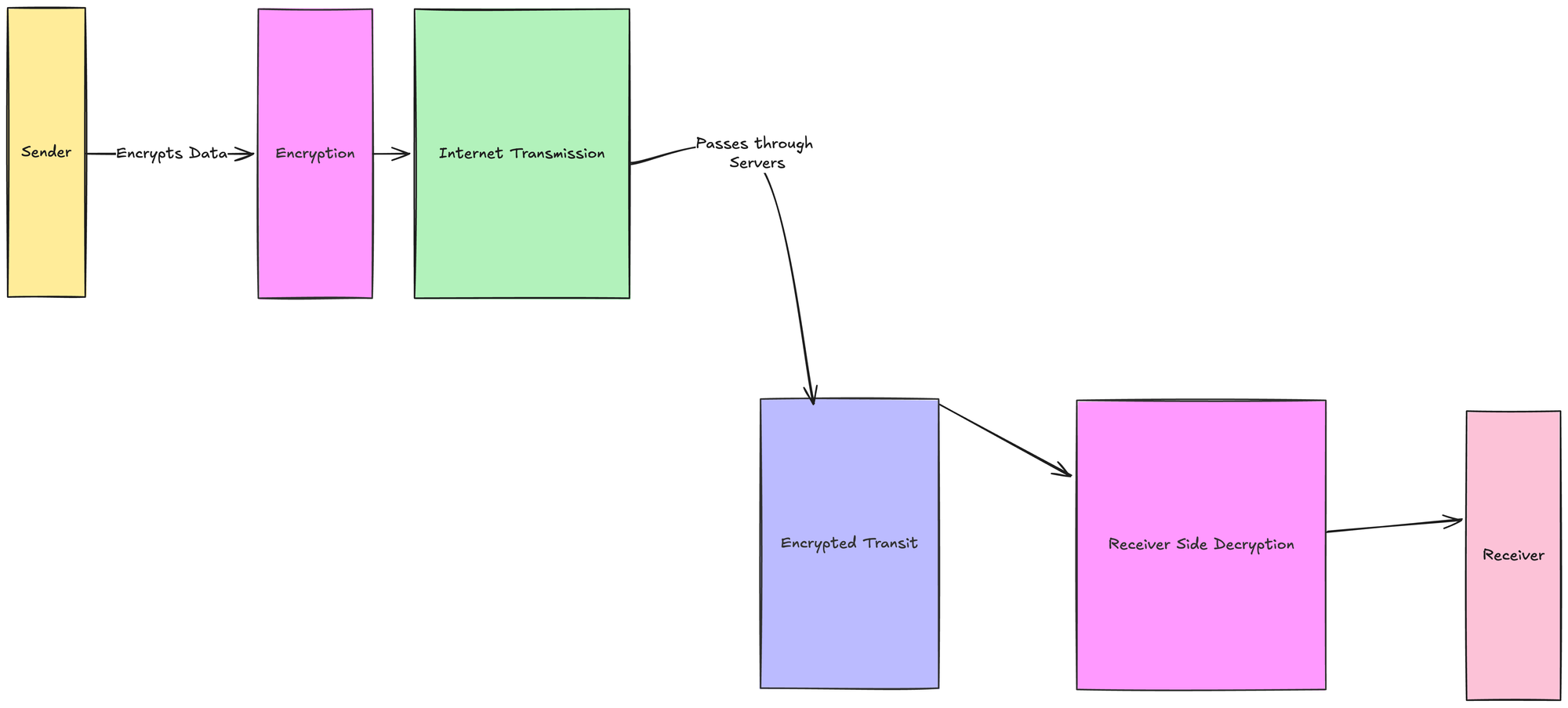
Cryptography
Cryptography is the study and practice of techniques of communication that is secure in the presence of adversaries
Cryptography involves generating codes and written data that allows the information to be kept a secret
Cryptography besides from hiding information can also be used for user authentication
Encryption Key
The Encryption key defines the encrypted output of a cryptographic alogorithm.
Using the key the plain text readable data is converted into cypertext that is encoded data
The encoded data can also be then converted into readable data by using the encryption key
In most encryption algorithms the keys are chosen using a large random numbers by the encrytion software and thus are very difficult to guess
Decryption
The Decryption is the provess of converting encrypted data that is cypertext into the original data
This process requires the encryption key and the decryption algorithm to decrypt the data
The data needs to be decrypted before the user or the intended recipient can read it
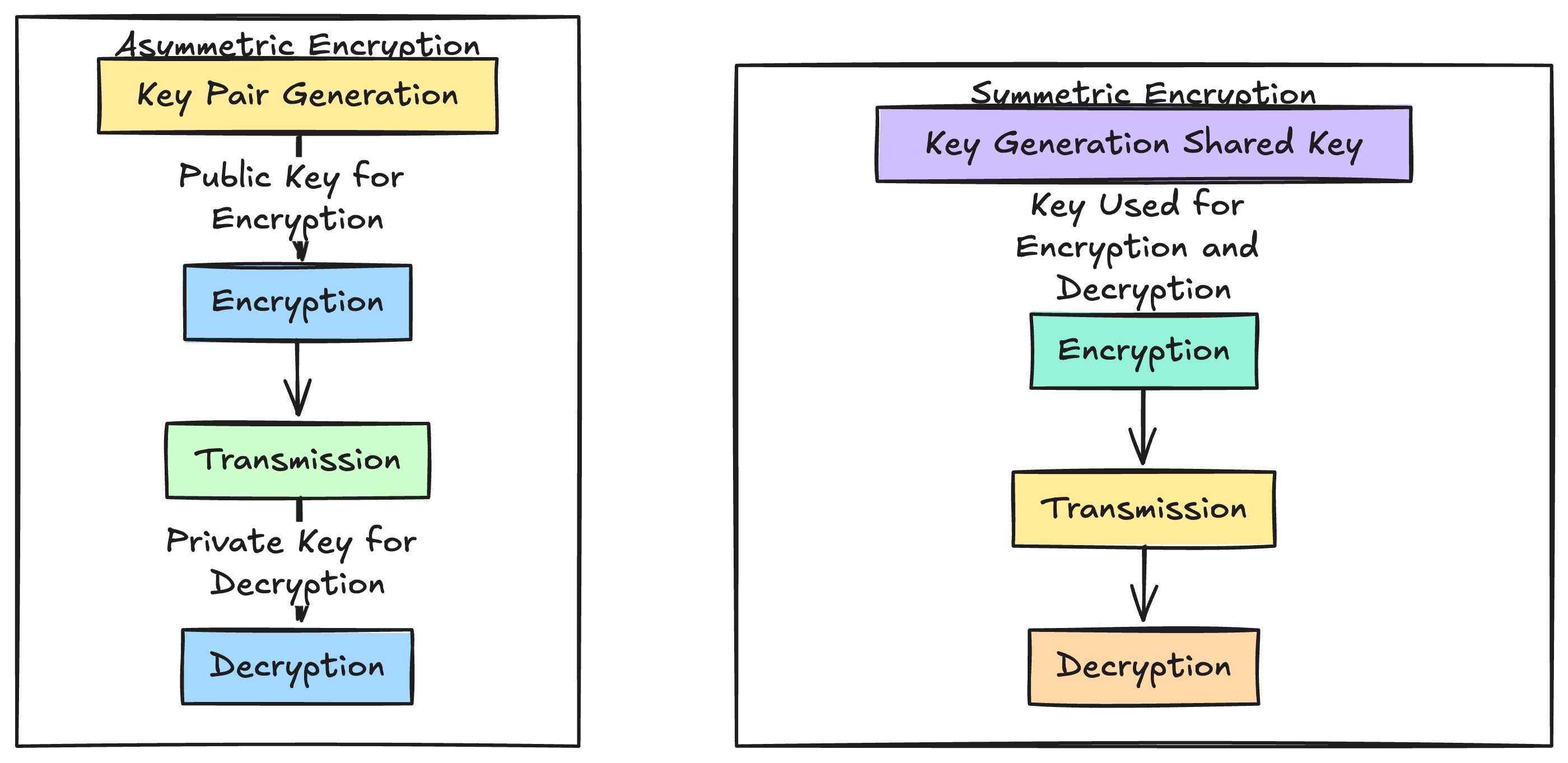
Symmetric Encryption
In Symmetrric encryption a single key is used to both encrypt the data and to decrypt the data
In symmetric encryption the same key needs to be shared between the sender and the recipient
The symmetric encryption is faster then asymmetric encryption but suffers from potential drawbacks from security risks, if the key is intercepted.
Asymmetric encryption
In the asymmetric encryption there are two keys one is a private key and another one is the public key.
The public key is shared with everyone and the private key is kept private.
Here the data is encrypted with the public key but it can only be decrypted with the private key.
This method is used in internet communications and provides a good security mechanism for video communications.
Public Key Infrastructure (PKI)
Public Key infrastrature is a set of roles, software and hardware that are designed to create and manage digital certificates for public key encryption
The purpose of the KPI is to facilitate secure transfer of information for a range of network activities
Digital Signature
Digital signature is an encryption technique that ensures that data has not been altered in transit.
The digital signature can be varified by anyone that has the pubic key of the signer
Metered TURN servers
- API: TURN server management with powerful API. You can do things like Add/ Remove credentials via the API, Retrieve Per User / Credentials and User metrics via the API, Enable/ Disable credentials via the API, Retrive Usage data by date via the API.
- Global Geo-Location targeting: Automatically directs traffic to the nearest servers, for lowest possible latency and highest quality performance. less than 50 ms latency anywhere around the world
- Servers in all the Regions of the world: Toronto, Miami, San Francisco, Amsterdam, London, Frankfurt, Bangalore, Singapore,Sydney, Seoul, Dallas, New York
- Low Latency: less than 50 ms latency, anywhere across the world.
- Cost-Effective: pay-as-you-go pricing with bandwidth and volume discounts available.
- Easy Administration: Get usage logs, emails when accounts reach threshold limits, billing records and email and phone support.
- Standards Compliant: Conforms to RFCs 5389, 5769, 5780, 5766, 6062, 6156, 5245, 5768, 6336, 6544, 5928 over UDP, TCP, TLS, and DTLS.
- Multi‑Tenancy: Create multiple credentials and separate the usage by customer, or different apps. Get Usage logs, billing records and threshold alerts.
- Enterprise Reliability: 99.999% Uptime with SLA.
- Enterprise Scale: With no limit on concurrent traffic or total traffic. Metered TURN Servers provide Enterprise Scalability
- 5 GB/mo Free: Get 5 GB every month free TURN server usage with the Free Plan
- Runs on port 80 and 443
- Support TURNS + SSL to allow connections through deep packet inspection firewalls.
- Supports both TCP and UDP
- Free Unlimited STUN
Step By Step How encryption process takes place
- Data preparation:
The data that has to be encrypted is known a plaintext, which first needs to be prepared for encryption.
This often involves padding which is adding additional bits to the data to make its file size larger and suitable for encryption
If the file size is already large then this does not need to be done
- Key Generation:
Depending on what kind of encryption you are doing, different types of keys need to be generated
a single key will be generated for symmetric encryption and a pair of keys will be generated for asymmetric encryption. That is a public key and a private key
- Encryption:
The encryption alogorithm uses the key to transform the plaintext into an encrypted message, as we have already discussed one of many of the famous encryption algorithms can be used including AES
- Symmetric encryption:
In Symettric algorithms the same key is used to encrypt and dcrypt the plaintext. AES is one of the famous and most widely used symettric algorithm
- Asymmetric encryption:
In Asymmetric algorithm the public key is used to encrypt the data and the private key can be used to dycrpt the data.
RSA is a popular Asymmetric algorithm
4. Transmission:
Once encrypted the ecrypted data can be safely transmitted over any public data transmission channel like the internet
5. Decryption:
Once the encrypted text reaches its destination then it can be decrypted.
for symmetric encryption the same key can be used for encryption as well as decryption and for asymmetric encryption private key needs to be used for decryption
6. post processing:
After decryption if there is any padding done before the encryption and that needs to be removed then this is done in post processing
Importance of End to End Encryption in Video communication
End to End Encryption is very important in video communication for maintain integrity and confidentiality of data that is passing through public networks
Let us consider some real life scenarios to better understand this
Real Life Scenarios
- Confidential Business Meetings
In business, work from home and video conferencing has become a nessessory tools for businesses to function
Employees oftem discuss sensitive topixs related to the business like financial planning, strategic decisions, propritory innovations etc
Having End to End encryption gauranttee that the conversations remain confidential and only accessable to meeting participants.
The end to end encrytions project data from cyber criminals and evesdroppers and even competitors
- Secure Government Communications
Goverment and its institutions regularly handle secure information that could have national security implications
End to End Encryption makes sure that this information is secure from foreign entities hackers and poeple who shoukd not have access to such information
- Healthcare Consultations
Telehealth has grown significantly, specially after covid. when doctors and patients are conversing that conversation is private health information
End to End encryption ensures that the conversation between health care providers and patients remain confidential and private
- Legal and Judicial Proceedings:
Legal proceedings are happening nowadays on video and these need to be protected from hackers and evesdroppers
Even client attorney conversations are privaleged and secrect in nature, thus end to end encryption ensures that these conversations remain private
- Media and Journalism
Media and Journalism is very imporatnt for democracies and the investigation that the journalists do, Often risking their lives in order for the truth to be known to the world.
This is private and confidential information that needs to be protected. The End to End Encryption ensures that the information is safe prying eyes and hackers and only the intented recipients have access to the information
Overview of Popular Encryption Algorithms used today
When implementing end to end encryption for video, you need to select the appripriate algorithm that will be suitable for your use-case
In this section we are going to go over some of the popular encryption algorithms and their pros and cons, also we are going to consider their suitability for video
1. Advanced Encryption Standard (AES)
AES is the gold standard of symeetric encryption, and it is widely used throughout the world
Pros
- Fast and very efficient, even more so for large amounts of data
- When implemented correctly it provides very strong security of data
- Nowadays, many devices support hardware accelaration for this encryption algorithms because of its popularity
- Different key sizes are available for different levels of security (128, 256, bits etc)
Cons
- This is a symettric algorithm thus requires key exchange between parties
- Managing the key can be complex in large systems
Suitability for video
It is very suitable for video and is already used widely in streaming protocols like HLS HTTP live streaming and Dynamic Adaptive streaming over HTTP (DASH)
2. RSA (Rivest-Shamir-Adleman)
RSA is an asymmetric encryption algorithm, it uses a public key to encrypt the data and a private key is need to decrypt the data
Pros
- Solves the key distribution problem that is faced by symmetrric algorithms
- Widely used and well understood
- Cna be used for digital signatures
Cons
- significantly slower than symettric algorithms
- Not suitable for large amounts of data
Suitability for video
This has limited suitability for video because it has slow speed for data encryption with large amounts of data
However it is widely used as a hybrid system for securely exchanging the keys for symetrric video encrytion over the internet
the key for symettic encryption is encrypted with RSA and exchanged over the internet with the destination
3. ChaCha20
ChaCha20 is newer encryption algorithm, that is suitable for mobile devices
Pros
- Fast and useful for mobile devices that lack hardware acceleration for AES
- Strong security
- Simple implementation
Cons
- Less widely adopted as compared to AES
- Limited hardware accelaeration support in most devices
Suitability for video
It is suitsble for video that is run on. mobile platforms. It can be a good choice for devices that lack hardware accelearation support for AES
4. Twofish
Twofish is a symettric block encryption algorithm, it is a successor to blowfish
Pros:
- Strong security
- Good design that allows for good performance on almost all devices
- Free to use and open source
Cons
- Less widely used as compared to AES
- Slightly slower than AES, because many machines have hardware acceleration build for AES
Suitability for video
It has good suitability for video, but many companies prefer AES because of wider support, hardware acceleration support and other factors
But it can work as an alternative to AES
you can also consider reading our other articles: