The Secure Real Time Transport Protocol is a cutting edge technology. The SRT protocol is designed to enable the secure and efficient data transmission over the internet
The SRT protocol was designed by Haivision, it is an Open source protocol made primarily for the real time video and data delivery purposes
High Quality, Low latency and secure transmission are the key features of this protocol
let us consider some of these and more key features below
How does SRT Protocol Work
Here are the Key features of the SRT Protocol
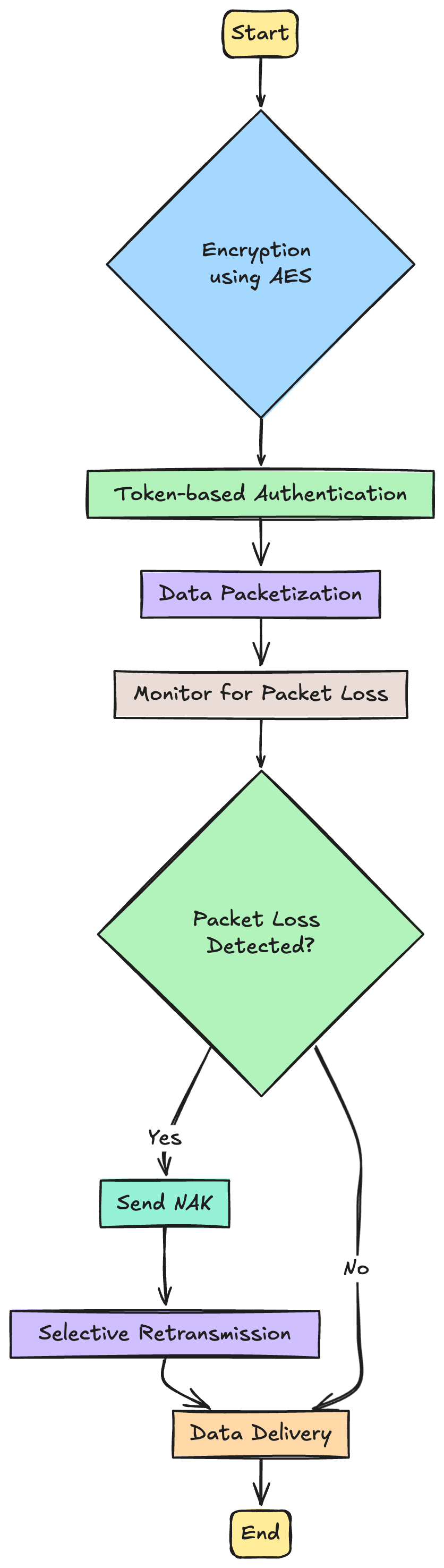
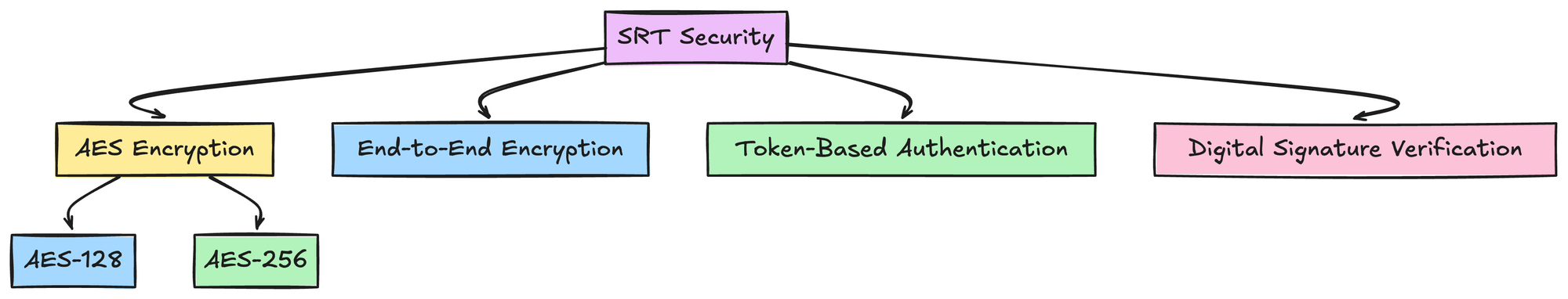
1. Security: How SRT Ensure the security of data during transmission
A. Encryption
- AES Encryption : These days data piracy has become rampant in the streaming industry.
Also, businesses want to keep their meetings secure in the remote working world, away from the compititors and hackers.
So as to keep data secure the SRT protocol has robust encryption mechanisms built in place.
The SRT protocol uses the AES Encryption or the Advanced Encryption Standard. This encryption standard is widely recognised to for being very robust and efficient
AES uses the AES-128 or the AES-256 bit encryption to provide strong defence against any unauthorized access
So, that no one can tamper with the data during transmission over the internet.
- End-to-End Encryption: With the SRT protocol the data is end to end encrypted which means that the data is encrypted from the sender all the way to the receiver
Even if the data is itnercepted it cannot be deciphered with the decryption key
B. Authentication
- Token Based Authentication: The SRT protocol has the token based authentication mechanism which verifies the identity of both the sender as well as the reciever of the transmission
Process:
A unique token is generated and it is shared between the sender and the reciver, This token is then used to authenticate the devices before anydata is hsared between them
- Digital Signature: SRT protocol uses the digital signature to verify the authenticity of the data that is being transmitted.
Process:
The sender signs the data with the senders public key and the reciver verifies the data using the senders public key
This gaurantees the integritiy and the origination of data( where the data originated, from the orignal sender and not from any other third party)
Verifying the digital signature ensures that the data has not been tampered with during transmission
2. Reliability: What mechanisms the SRT protocol uses to ensure reliable data transport
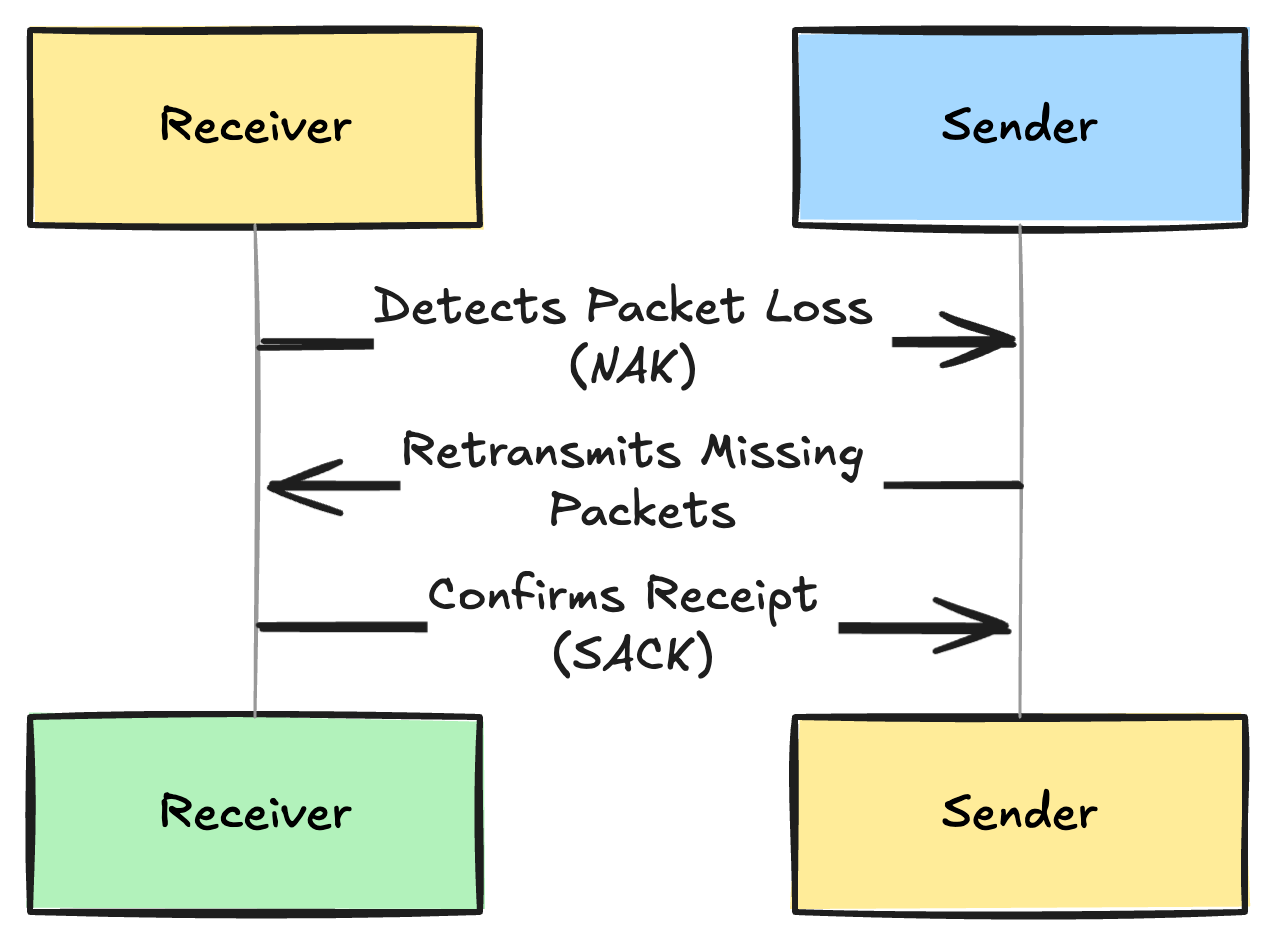
A. Packet Loss Recovery
- Retransmission Requests:
In the SRT protocol, the receiving client can request the retransmission of lost and corropted packets of data from the sender.
When a client detects that a packet of data is corropted or is missing then it sends a NAK or a Negative acknowledgement to the sending device prompting retransmission of data
Process:
the reciver contineously monitors the incoming packets of data and the sequence of these packets.
If there is a gap in the sequence the reciver sends a NAK request to the sender
- Selective acknowledgements (SACK):
When the receiving device sends a NAK the sender then only retransmits the packets that are missing thus improving efficiency and reducing the unnecessary data transmission
This is because of Selective acknowledgement that is built in the SRT protocol which enables both the devices to send and receive data effectively
Process:
The receiver sends a SACK request with sequence of numbers that signifies the successfully received packets and the missing packets.
This allows the sender to resend only the missing packets thus avoiding redundant data transfers between devices.
B. Error Correction
- Forward Error Correction (FEC):
SRT also has a awesome feature called as the Forward error correction mechanism. With FEC the SRT protocol preemptively sends redundant data to the stream
This data can be used by the receiver to reconstruct the missing packets or the corrupted packets without the need for retransmission by the sender.
Process:
Here the sender sends parity packets along the data streams based on the FEC algorithm
this allows the reciever to reconstruct the missing data using the partiy packets if some data is lost in transmission
3. Low Latency: How does SRT achieve Low Latency transmission
A. Optimized Buffering
- Dynamic Buffering:
SRT utilizes adaptive buffering strategie to minimize latency. The protocol dynamically adjusts teh bitrate of teh data stream in real time based on the current network bandwidth
this technology gives smooth video in fluctuating network bandwidth in usecases such as mobile devices or where the network is not proper
- Minimal Buffering:
The SRT protocol keeps the buffer size as small as possible without compromising reliability, SRT can achieve lower latency compared to traditional protocols
B. Real-Time Transport Protocl (RTP) Compatibility
- RTP over SRTP:
SRT can transport RTP streams. The RTP is designed for real time data transmission
The compatibility allows SRT to leverage RTP real time capability, this further reduces the latency and enhancing the user experience for live experience.
Network Adaptibility: How SRT works in varying network conditions
A. Adaptive Bitrate Streaming
- Dynamic Bitrate adjustment:
SRT adjusts the bitrate of the video streams automatically according to the network conditions, if there is ample bandwidth the SRT will automatically start streaming high quality video
On the other hand if the quality of the bandwidth decreases because of congestion or if the user has variable bandwidth if they are on mobile data then the SRT protocol provides a smooth video stream but slightly lower bitrate so that the video does not buffer.
- Congestion control:
The SRT has a mechanism where it has algorithms that monitor network traffic and adjusts the data transmission accordingly.
Thus SRT tries to prevent network congestion and maintains a smooth data flow
B. Resilience to Jitter and Packet Delay Variation
- Jitter Buffer:
SRT incorporates a jitter buffer in order to compensate for packet delay variations (jitter) in the network.
This buffer acts as a storage for incoming packets and stores them, then it reorders the packets if they arrive out of sequence, thus ensure smooth data delivery and a smooth stream of video.
- Time Stamp Based Synchronization:
the SRT protocol uses the time stamp in order to determine the sequence of packets arriving and manages the out of order delivery of data
Thus the SRT protocol reconstructs the data correctly and in the right order.
C. Error resilience
- Redundant Data Transmission:
In situations where data transmission is jittery and inconsistant the SRT protocol transmits redundant data to ensure that if if some packets of data are lost or are corropted still the video stream is uninterrupted
- Network Path Diversity:
The SRT protocol has network path diversity where in it can use multiple internet connections and mutiple internet paths to reach the destination or the client devices
This is helpful when one internet connection or one internet path is slow etc.
Comparison with Traditional Protocols: SRT vs RTMP, HTTP and WebRT
SRT ( Secure Real Time Transport)
SRT protocol is the modern protocol designed with secure , reliable and low latency video, audio and data streaming over unreliable network conditions
It has many good features that are required for modern day data transmission but requires skill because of complexicity involved in implementation
RTMP (Real Time Messaging Protocol)
RTMP is the real time messaging protocol. It was designed by Adobe for streaming audio, video and data over the internet
It is widly used for live streaming and on demand media delivery.
2. HTTP (Hypertext Transfer Protocol)
HTTP is a basic protocol that was developed with browsing the internet and goign to websites etc
3. WebRTC (Web Real-Time Communication)
WebRTC is a collection of communication protocols and APIs that enable real time communication, video and audio streaming between browsers adn devices
Advantages and disadvantages
| Protocol | Advantages | Disadvantages |
|---|---|---|
| SRT (Secure Real Time Transport) | Data security with AES 128 bit and AES 256 bit encryption. | Difficult implementation and management. |
| Token based Auth mechanism | Overhead from error correction and retransmission mechanisms | |
| Packt loss recovery and smooth data transmission with NAK and SACK | ||
| Dynamic buffering and low latency | ||
| Adaptive bitrate streaming that adjusts according to Network conditions | ||
| Resilient to Network Jitter and congestion | ||
| Highly Scalable | ||
| Open Source | ||
| RTMP Real Time Messaging protocol | Supports basic security mechanisms RTMPS | Outdated security measures |
| Suitable for live streaming | less efficient packet loss handling | |
| Established protocol with wide CDN support | Less adaptability to varying network conditions as compared to SRT protocol. | |
| HTTP (Hypertext Transfer Protocol) | Highly reliable and traditional data tranfer protocol | Not designed for low latency and real time streaming |
| universally supported | Non adaptive to changing network conditions | |
| CDN support available | ||
| WebRTC (Web Real-Time Communication) | Built for video calling applications | Requires TURN servers for large deployments |
| Secure protocol with built in encryption using DTLS SRTP | ||
| Designed with low latency and real time video communication | ||
| Adapting to varying network conditions | ||
| WebRTC (Web Real-Time Communication) |
Metered TURN servers
- API: TURN server management with powerful API. You can do things like Add/ Remove credentials via the API, Retrieve Per User / Credentials and User metrics via the API, Enable/ Disable credentials via the API, Retrive Usage data by date via the API.
- Global Geo-Location targeting: Automatically directs traffic to the nearest servers, for lowest possible latency and highest quality performance. less than 50 ms latency anywhere around the world
- Servers in all the Regions of the world: Toronto, Miami, San Francisco, Amsterdam, London, Frankfurt, Bangalore, Singapore,Sydney, Seoul, Dallas, New York
- Low Latency: less than 50 ms latency, anywhere across the world.
- Cost-Effective: pay-as-you-go pricing with bandwidth and volume discounts available.
- Easy Administration: Get usage logs, emails when accounts reach threshold limits, billing records and email and phone support.
- Standards Compliant: Conforms to RFCs 5389, 5769, 5780, 5766, 6062, 6156, 5245, 5768, 6336, 6544, 5928 over UDP, TCP, TLS, and DTLS.
- Multi‑Tenancy: Create multiple credentials and separate the usage by customer, or different apps. Get Usage logs, billing records and threshold alerts.
- Enterprise Reliability: 99.999% Uptime with SLA.
- Enterprise Scale: With no limit on concurrent traffic or total traffic. Metered TURN Servers provide Enterprise Scalability
- 5 GB/mo Free: Get 5 GB every month free TURN server usage with the Free Plan
- Runs on port 80 and 443
- Support TURNS + SSL to allow connections through deep packet inspection firewalls.
- Supports both TCP and UDP
- Free Unlimited STUN
Consider reading our other excellent articles
