STUN is a protocol that is designed to overcome barriers in communication that are introduced by NAT.
STUN protocol enables devices that are behind a NAT to discover their own public IP address and port number.
The devices communicate with a STUN server that is on the internet, and the STUN server provides this information to the client device
The device can then share this information with another device or devices on the Internet with which it wants to communicate
This allows external devices to communicate with each other directly, effectively traversing the NAT
STUN is important in facilitating peer-to-peer communication in real time.
If you want to know more about what is a STUN server, then you can refer to our article: Stun Server: What is Session Traversal Utilities for NAT?
Understanding the NAT Problem
Explanation of Network Address Translation (NAT) and its widespread use.
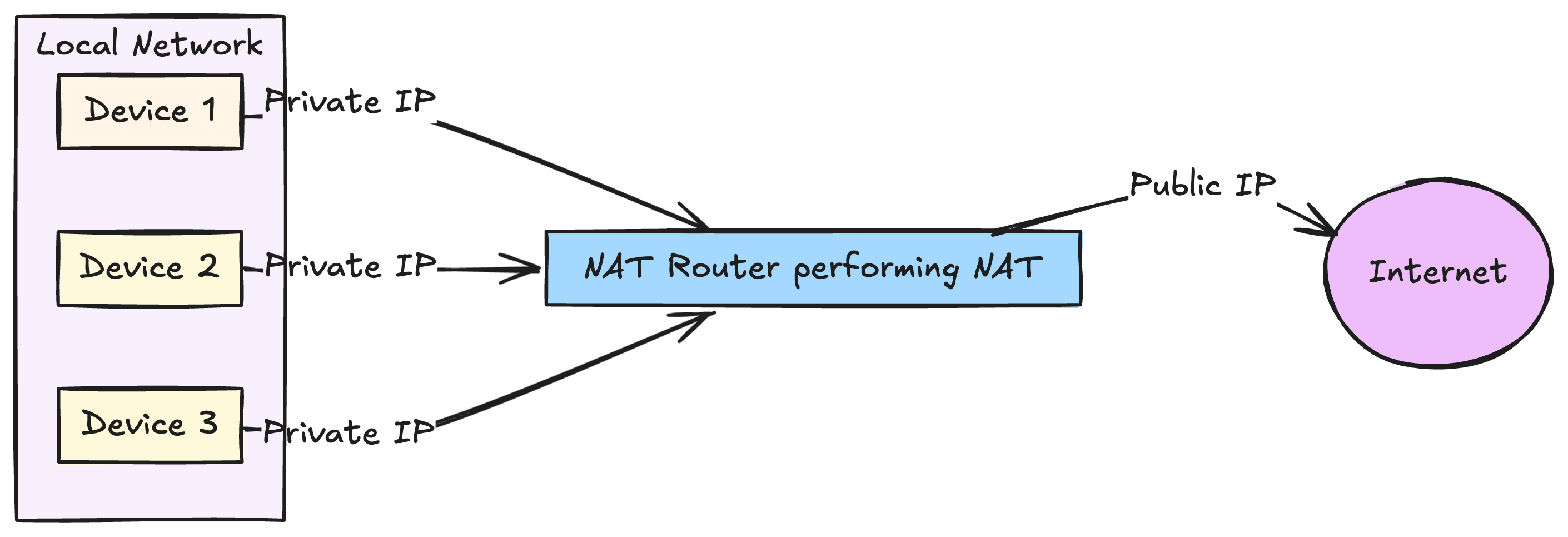
Routers map multiple private IP addresses to a single IP public IP address using a technique called NAT or Network Address Translation
This allows multiple devices that are on the local network to connect to the internet using a single public IP.
Thus conserving the limited number of IPv4 addresses.
NAT become widespread due to exponential growth in devices that were connected to the internet and there was a delay in adopting IPv6 which offers a larger address space.
Issues Introduced by NAT in peer-to-peer communication
NAT blocks direct communication between devices by blocking inbound traffic, altering the port mappings and hiding the public IP address from the devices that are behind the NAT
Thus overcoming barriers created by NAT is important for enabling direct communication between devices that are on different networks across the internet
NAT transversal solutions like STUN protocol allow devices to discover their own public IP address and negotiate connections through NAT routers
Many times STUN servers are not enough for NAT traversal and you need to fallback on TURN servers
If you are implementing one to one communication and need a reliable STUN and TURN servers then you can consider
Open Relay Project: Free TURN / STUN servers
Metered.ca TURN servers: Premium TURN servers with global reach
Services like VoIP and Video conferencing require STUN and TURN servers.
STUN Protocol: Solution for NAT Traversal
What is STUN?
STUN or Session Traversal Utilities for NAT is a standardized protocol that is defined in the RFC 5389 that enables devices that are behind a NAT or firewall to discover their own public IP address and PORT number
STUN also lets devices and applications discover what kind of NAT they are behind and obtain the necessary information to establish a direct communication channel with other devices on the internet
The core functionalities of STUN include:
- Public IP address discovery: STUN allows a client device to learn its public IP address
- Port Mapping: STUN helps the client device know what port number it has been assigned by the NAT device
- NAT type detection: The STUN server helps client device know what kind of NAT device it is behind. NAT types include full cone NAT, restricted cone NAT, symmetric NAT etc
- Facilitating Peer-to-Peer Communication: Thus the STUN server facilitates peer-to-peer communication between devices
How STUN Works
How STUN helps devices to Discover their own Public IP Address and Port number
When a client device sends a request to the STUN server, which is on the internet. The STUN server can see the public IP address and port number from which the request is coming from.
The STUN server then sends this information back to the client. This is how the STUN server helps devices discover their own public IP and port number that is assigned to them by the NAT router.
The process enables the client to
- Learn its public endpoint: Understand how other devices see it on the internet
- Share correction details with peers: Once the client device gets the details from the STUN server, it can then share it with other devices on the internet with which it wants to start communication
- Adapt NAT behaviour: Adjust strategies on how to traverse the NAT based on what type of NAT the client device is behind
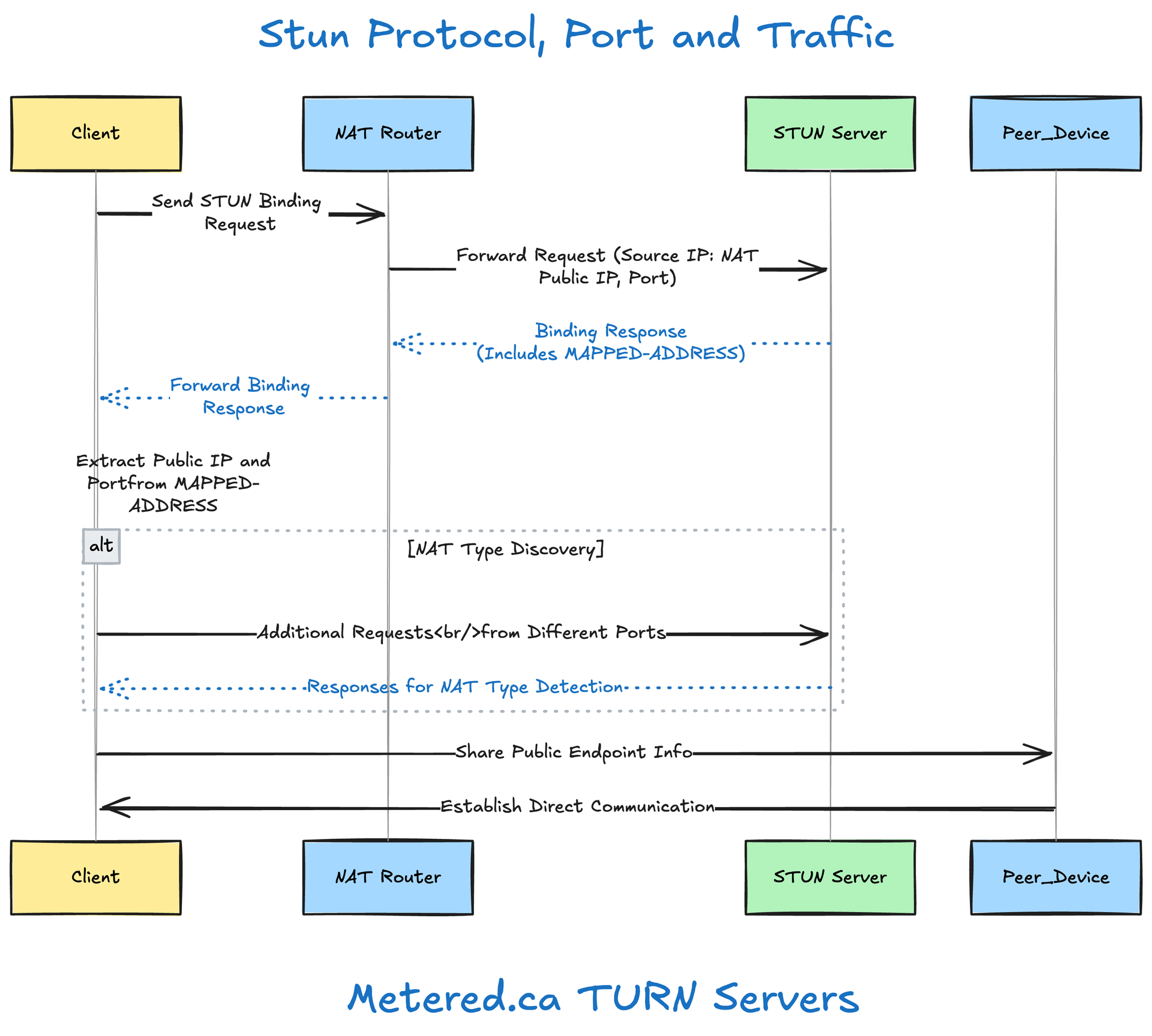
Step by Step how STUN works
- Client Initiation
- The client device sends a request to the STUN server using the UDP protocol to learn its own public IP address and port number
- It sends a STUN binding request over UDP User datagram protocol
- STUN server reception
- The STUN server accepts the request and notes the source IP and port number from which the request is coming from.
- The STUN server then responds back with the IP address and port number, back to the client
- Binding response
- The STUN server contracts a STUN binding response message
- This response includes a MAPPED-ADDRESS attribute, client public IP address and port.
- Client receipt
- The client device then receives the binding response from the server
- The client device then retrieves the Public IP and port number from the MAPPED-ADDRESS attribute
- NAT type discovery (optional):
- The client can then perform additional tests from different STUN servers to determine what type of NAT the client is behind
- This involves sending different requests from different ports and evaluating the response
- Establishing communication
- With the public IP address and port number, the client device can then share this information with other devices on the internet to establish communication
DIAGRAM Here
STUN vs TURN and ICE Protocol
STUN vs other NAT Traversal Methods
- STUN ( Session Traversal Utilities for NAT)
- Purpose: Enables the client devices to discover their public IP and port number
- Use-Case: Good for when NAT and firewalls allow for peer-to-peer direct communication after public IP addresses are known.
- Limitations: Does not work when NAT and firewall rules are restrictive.
- TURN (Traversal Using Relays around NAT)
- Purpose: Provides a fallback mechanism by relaying the data through a TURN server when peer to peer direct communication is not possible
- Use-Case: Essential when restrictive NAT and firewall rules does not allow direct communication between devices on the internet
- Operation: All the traffic is end to end encrypted and send through the TURN server, which relays the data to each client
- Trade-Offs: You need turn servers near the client devices, in order to reduce latency and improve communication
- ICE (Interactive Connectivity Establishment)
- Purpose:ICE is a framework that combines STUN and TURN to establish the best possible connection between clients.
- Use-Case: Used in WebRTC and other real time communication systems in order to handle various network configurations
- Operation
- Candidate Gathering: Clients first gathers candidates to see possible endpoint connections, these are found using host, reflexive via STUN and TURN
- Connectivity checks: Clients then perform checks to see using which candidates they can establish a connection
- Candidate selection: The optimal path that is the one with the lowest latency is selected by the ICE framework for establishing the communication
- Advantages: Maximizes the chances of establishing a connection while optimizing for best performance
When to use STUN over other methods
- Use STUN alone when
- Both the clients are behind NAT and firewall that enable direct communication after discovering the IP address and port number
- Both the clients have good internet connection and the network environment is predictable, for example devices are not changing their networks like in the case of mobile phones etc
- Use STUN TURN and ICE when
- The devices are behind restrictive NAT and firewall rules
- The network environment is changing like in case of mobile devices etc
- Reliability is important, you cannot have devices disconnecting for some reason or the other
Summary of Considerations
- Performance
- STUN gives good performance when connecting nearby clients but it is not reliable as well, but it is a free option
- TURN gives the best performance but needs a server nearer to client devices to reduce latency. Nowadays, you have global turn server services such as metered.ca which work quite well
- Complexity:
- STUN is quite simple to implement and use
- TURN: It is quite simple and easy to use
- Success Rate:
- STUN: It will fail in restrictive NAT and firewall rules
- TURN: More reliable and works with restrictive NAT and firewall rules
STUN Ports and traffic handling
Default port used by STUN
Commonly used UDP and TCP Ports are 3478 and 5349
The STUN protocol uses specific network ports to communicate between clients and STUN servers
- UDP Ports
- Port 3478: This is the default port for STUN for the UDP protocol, STUN generally operates over the UDP protocol because of its low overhead nature and port 3478 is usually used
- Port 5349: This is generally the port for UDP over DTLS, which provides encryption for UDP communication
- TCP Ports
- Port 3478: STUN : STUN can operate on the same port that is 3478 for TCP when UDP is not suitable or blocked
- Port 5349: This is used for STUN with TLS that is Transport Layer Security offering TCP connections
- Alternate ports
- While these are the default ports for STUN server, any other port can also be configured to be used for STUN and TURN servers.
- For security reasons it is often advisable as well to run STUN server on other ports.
Security Considerations with Port usage
- Exposure to port scanning
- Attackers often scan the internet for default ports for STUN server, keeping STUN servers on default port may make then more susceptible to such reconnaissance activities
- Firewall Configuration
- Inbound traffic
- By default many firewalls block unsolicited inbound traffic on STUN ports in order to prevent unauthorized access
- The firewalls only allow inbound traffic, if it is in response to a legitimate request that has been initiated by a device inside the network
- Outbound traffic:
- Permit outbound traffic to only trusted STUN and TURN server and on ports that are necessary.
- Inbound traffic
- Using Encryption
- STUN over TLS/DTLS (ports 5349): While the TURN server traffic is end-to-end encrypted. STUN server traffic is not, but you can enable the STUN encryption as well.
- Regular Updates and patches: When you are running your own STUN/TURN servers you need to regularly update them and patch them for security.
- Logging and monitoring: Always log and monitor STUN and TURN servers if you are running your own STUN/TURN servers for security venerabilities
Cloud based STUN Servers vs Self Hosted Solutions
Cloud based TURN servers
- Metered TURN/STUN servers: Offers Global, scalable, managed STUN and TURN services with API
- Google Public STUN servers: Google offers a list of free STUN servers, you can get the list of Google STUN servers
- Open Relay TURN / STUN servers: Free TURN servers for the public
Self Hosted Solutions
- Coturn STUN / TURN servers: You can run your own turn server with the open source project cotton. Here is the guide on : How to setup and configure TURN server using coTURN?
- AWS TURN servers: You can run coturn on AWS as well: Here is the guide on that: AWS TURN server: In 7 Simple Steps
- Azure TURN servers: You can run the TURN servers on Azure as well. Here is a guide on that: Azure TURN Server: The Step by Step Guide.
- TURN server costs: here is a guide on potential costs and considerations when running your own TURN server: TURN Server Costs: A Complete Guide
- API: TURN server management with powerful API. You can do things like Add/ Remove credentials via the API, Retrieve Per User / Credentials and User metrics via the API, Enable/ Disable credentials via the API, Retrive Usage data by date via the API.
- Global Geo-Location targeting: Automatically directs traffic to the nearest servers, for lowest possible latency and highest quality performance. less than 50 ms latency anywhere around the world
- Servers in all the Regions of the world: Toronto, Miami, San Francisco, Amsterdam, London, Frankfurt, Bangalore, Singapore,Sydney, Seoul, Dallas, New York
- Low Latency: less than 50 ms latency, anywhere across the world.
- Cost-Effective: pay-as-you-go pricing with bandwidth and volume discounts available.
- Easy Administration: Get usage logs, emails when accounts reach threshold limits, billing records and email and phone support.
- Standards Compliant: Conforms to RFCs 5389, 5769, 5780, 5766, 6062, 6156, 5245, 5768, 6336, 6544, 5928 over UDP, TCP, TLS, and DTLS.
- Multi‑Tenancy: Create multiple credentials and separate the usage by customer, or different apps. Get Usage logs, billing records and threshold alerts.
- Enterprise Reliability: 99.999% Uptime with SLA.
- Enterprise Scale: With no limit on concurrent traffic or total traffic. Metered TURN Servers provide Enterprise Scalability
- 5 GB/mo Free: Get 5 GB every month free TURN server usage with the Free Plan
- Runs on port 80 and 443
- Support TURNS + SSL to allow connections through deep packet inspection firewalls.
- Supports both TCP and UDP
- Free Unlimited STUN
You can consider some of our other articles: